Latest
TECH NEWS
How To
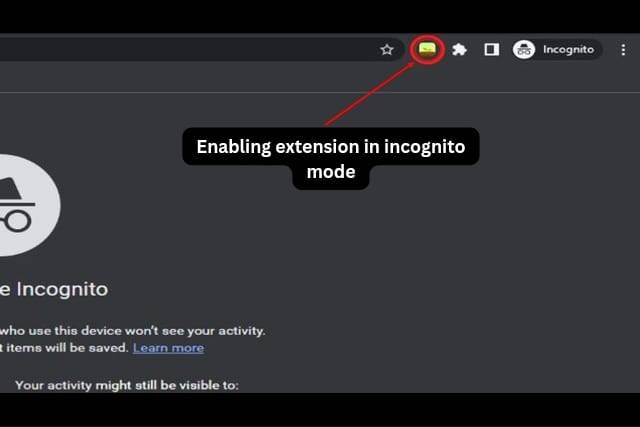
How to Use Extensions in Incognito Mode in Google Chrome
In this guide, we will explore how to use extensions in Incognito mode in Google…
Is it Possible to Install Windows on a Mac and How to Do It
Table of Contents[Open][Close]Is it Possible to Install Windows on a Mac and How to Do…
Solving Business Problems with the Right Software Vendor: How to Make the Right Choice
Businesses of all sizes and industries rely on software solutions to improve efficiency, automate processes,…
DIY Cleaning: How to Remove Smudges and Fingerprints from Your Mobile or Smart Device Screen
Keeping your mobile or smart device screens clean is important for both appearance and functionality.…
How to Take a Video and a Screenshot on a PS5
You can use your controller to precisely record what’s happening on your PlayStation 5’s screen…
Windows 11: How to Move a Window to a Different Monitor
It is simple to move an existing app window between two or more displays on…
How to Avoid Desktopanalyticscenter dot site Pop-Ups? explain step by step
How to Avoid Desktopanalyticscenter dot site Pop-Ups DesktopAnalyticsCenter.site is a website that displays pop-up advertisements.…
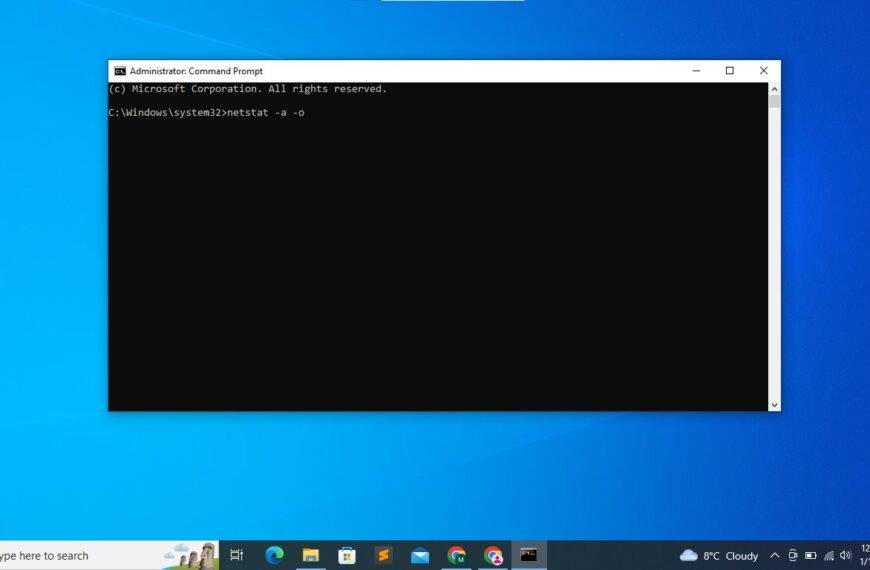
How to open TCP and upd port in Windows 10 using command Prompt
Introduction In this article, we will show you how to open TCP and UDP ports…
How to Type Faster: 5 Tips to Increase Your WPM
How to Type Faster: 5 Tips to Increase Your WPM Are you looking to increase…
Apple
Windows vs MacOS: Which Operating System is Right for You?
Windows vs MacOS: Which Operating System is Right for You?User InterfaceCompatibilitySecurityPriceFinal Thoughts Windows vs MacOS:…
How to Set Up and Customize Your Apple Watch
How to Set Up and Customize Your Apple WatchSet up your Apple WatchCustomize your watch…
How to Troubleshoot Common iPhone Issues
How to Troubleshoot Common iPhone IssuesBattery Life IssuesSlow PerformanceWi-Fi Connectivity IssuesApp CrashesFrozen ScreenUnable to Send…
Seamless File Transfer: A Guide to Sharing Files between Mac and Windows PC
Seamless File Transfer: A Guide to Sharing Files between Mac and Windows PCUse a USB…
The Best iPad Accessories for Productivity and Entertainment
The Best iPad Accessories for Productivity and EntertainmentProductivity Accessories:Apple Pencil Keyboard CaseUSB-C HubStandEntertainment Accessories:HeadphonesGame Controller…
10 Best Hidden Mac Shortcuts You Need to Know
10 Best Hidden Mac Shortcuts You Need to KnowTake a Screenshot:Force Quit Applications:Switch Between Applications:Cycle…
Apple Support: Get Expert Assistance for Your Apple Devices and Services
Apple Support: Get Expert Assistance for Your Apple Devices and ServicesOnline SupportPhone SupportIn-Person AssistanceAppleCareConclusion Apple…
How Apple Watch is the Only Wearable Device You’ll Ever Need
How Apple Watch is the Only Wearable Device You’ll Ever NeedDesign and DisplayFeaturesHealth and FitnessAppsBattery…
Unleashing Your Inner Photographer: A Guide to Apple’s Camera Features
Table of Contents[Open][Close]Unleashing Your Inner Photographer: A Guide to Apple’s Camera FeaturesCamera Features of Apple…
Windows
How to troubleshoot file or folder permission errors in cloud storage services like Dropbox, OneDrive, or Google Drive
How to troubleshoot file or folder permission errors in cloud storage services like Dropbox, OneDrive,…
Windows vs MacOS: Which Operating System is Right for You?
Windows vs MacOS: Which Operating System is Right for You?User InterfaceCompatibilitySecurityPriceFinal Thoughts Windows vs MacOS:…
Seamless File Transfer: A Guide to Sharing Files between Mac and Windows PC
Seamless File Transfer: A Guide to Sharing Files between Mac and Windows PCUse a USB…
10 Tips for Optimizing Your Windows PC’s Performance
10 Tips for Optimizing Your Windows PC’s PerformanceRemove Unnecessary Programs and FilesRun Disk Cleanup and…
10 Essential Tips for Using Microsoft Word Like a Pro
10 Essential Tips for Using Microsoft Word Like a Pro 10 Essential Tips for Using…
Protecting Computer and Personal Data: Best Practices for Securing Windows 10
Protecting Computer and Personal Data: Best Practices for Securing Windows 10Keep your Windows 10 updatedUse…
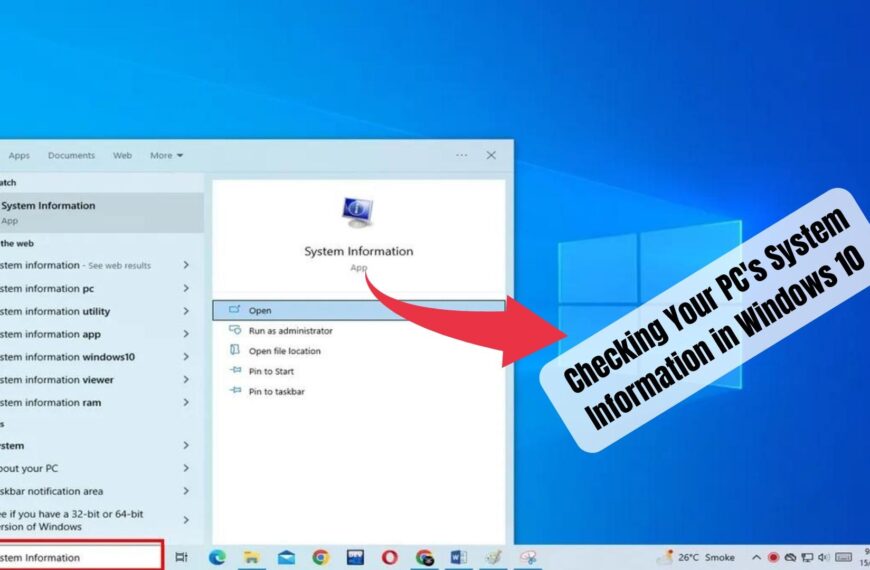
How to Check Your PC’s System Information in Windows 10
Table of Contents[Open][Close]How to Check Your PC’s System Information in Windows 10Step 1: Open the…
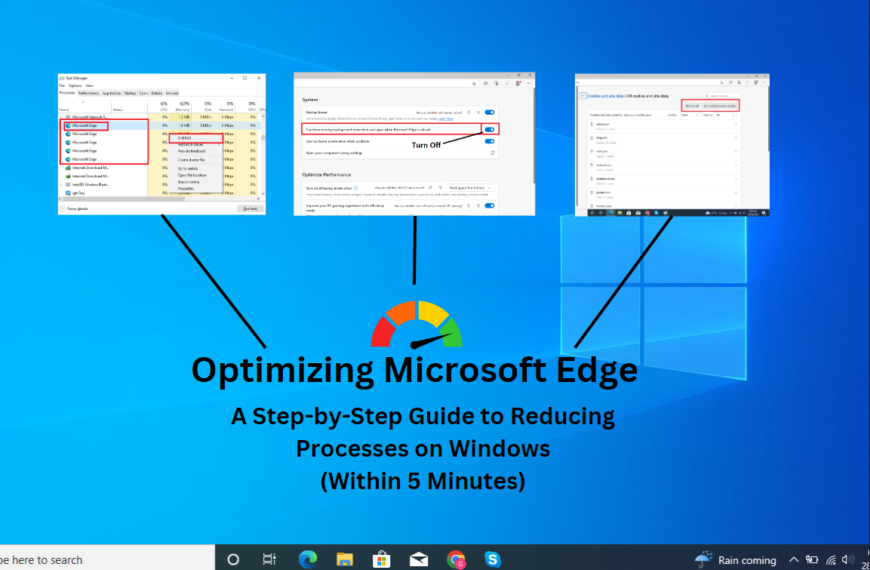
Optimizing Microsoft Edge: A Step-by-Step Guide to Reducing Processes on Windows
Table of Contents[Open][Close]A Step-by-Step Guide to Reducing Processes on WindowsStep 1: Open Task ManagerStep 2:…
5 Useful Windows Features You Might Have Overlooked in Windows 10
5 Useful Windows Features Windows is a powerful and feature-rich operating system, but many of…
Software u0026amp; Apps
App Security: Protecting User Data in the Mobile Era
App Security: Protecting User Data in the Mobile EraThe Significance of App SecuritySecure Data TransmissionAuthentication and AuthorizationData EncryptionSecure Backend InfrastructureRegular Security Audits and TestingPrivacy Policy and User ConsentOngoing Security Updates…
Software Engineering: Building the Foundations of Innovation
Software Engineering: Building the Foundations of InnovationThe Essence of Software Engineering:Key Principles of Software Engineering:Role of Software Engineering in Innovation:Evolving Practices and Trends:Conclusion Software Engineering: Building the Foundations of Innovation…
App Monetization: Strategies for App Success
App Monetization: Strategies for App SuccessChoose the Right Monetization ModelIn-App AdvertisingIn-App PurchasesSubscriptionsSponsorships and PartnershipsPrioritize User ExperienceOptimize for App Store Optimization (ASO)Leverage User AnalyticsExplore Alternative Revenue StreamsData MonetizationAffiliate MarketingIn-App SponsorshipsConclusion App…
App Revolution: Transforming Everyday Life
App Revolution: Transforming Everyday LifeCommunication and ConnectivityWork and ProductivityLearning and EducationShopping and E-commerceEntertainment and LeisureConclusion App Revolution: Transforming Everyday Life The rise of mobile applications has brought about a significant…
CYBER SECURITY
Strengthening Data Protection with Digital Security Controls
Digital Security ControlsThe Significance of Data ProtectionPreserving Customer Trust Regulatory ComplianceIntellectual Property ProtectionMitigating Financial LossesStrengthening…
Securing Your Home: A Guide to Digital Security Systems
Digital Security SystemsThe Importance of Home SecurityCrime DeterrencePrompt Response to EmergenciesPeace of MindRemote MonitoringChoosing the…
Securing IoT Devices with Aura Digital Security Solutions
Aura Digital Security SolutionsThe Importance of IoT Device Security:Securing IoT Devices with Aura Digital Security…
Securing Cloud Environments with Digital Security Controls
Digital Security ControlsThe Significance of Cloud Security The importance of cloud security is highlighted by…
Safeguarding Your Business: Fortifying with Digital Security Measures
Digital Security MeasuresThe Growing Significance of Digital Security for BusinessesDigital Security Measures for Business ProtectionConclusion…
Safeguarding Critical Infrastructure with Digital Security Measures
Digital Security MeasuresThe Importance of Critical Infrastructure ProtectionDigital Security Measures for Critical Infrastructure ProtectionConclusion Digital…
Protecting Intellectual Property with Digital Security Measures
Digital Security MeasuresThe Value of Intellectual PropertyDigital Security Measures for Intellectual Property ProtectionData EncryptionAccess ControlNetwork…
Navigating the Complexities of Digital Security Management
Digital Security ManagementThe Digital Security Management LandscapeDiverse Threat LandscapeRapid Technological AdvancementsHuman FactorsRegulatory ComplianceBalancing Usability and…
Key Features and Benefits of Digital Security Controls Products
Digital Security Controls ProductsAdvanced Threat Detection and PreventionRobust Firewall and Network SecurityData Encryption and ProtectionEndpoint…